“Phishing” is any communication, usually an email, that tries to lure you into revealing login credentials, financial information or other confidential details. Unfortunately, it is becoming more and more common.
A State of Phishing report from security firm SlashNext claims that there were more than 255 million phishing attacks in 2022, a 61% increase from the year before. Luckily, according to the Verizon Data Breach Investigations Report for 2022, only 2.9% of employees click through from phishing emails, but with hundreds of millions of email addresses targeted, the raw numbers are still high. We’ve been noticing—and hearing from clients—that phishing emails are also slipping through spam filters more than in the past.
To help you avoid falling prey to phishing tricks, check out our example screenshots below from real phishing emails, complete with annotations calling out the parts of a message that give it away as fake. All phishing emails are trying to lure you into clicking a link or button to a website that will encourage you to enter your password or other confidential information. If you realize that a message is a phishing attack, you won’t get suckered into clicking a link or revealing your personal information.
Fake Password Expiration Scam
Our first example is a password expiration scam—it’s trying to get you to click a button to keep your password from expiring. What’s ironic about this scam is that passwords should never expire—forcing users to change them regularly is terrible security practice. If a password is strong and unique, there is no reason to change it unless the site suffers a breach. Let’s look at what identifies this message as a phishing attack.
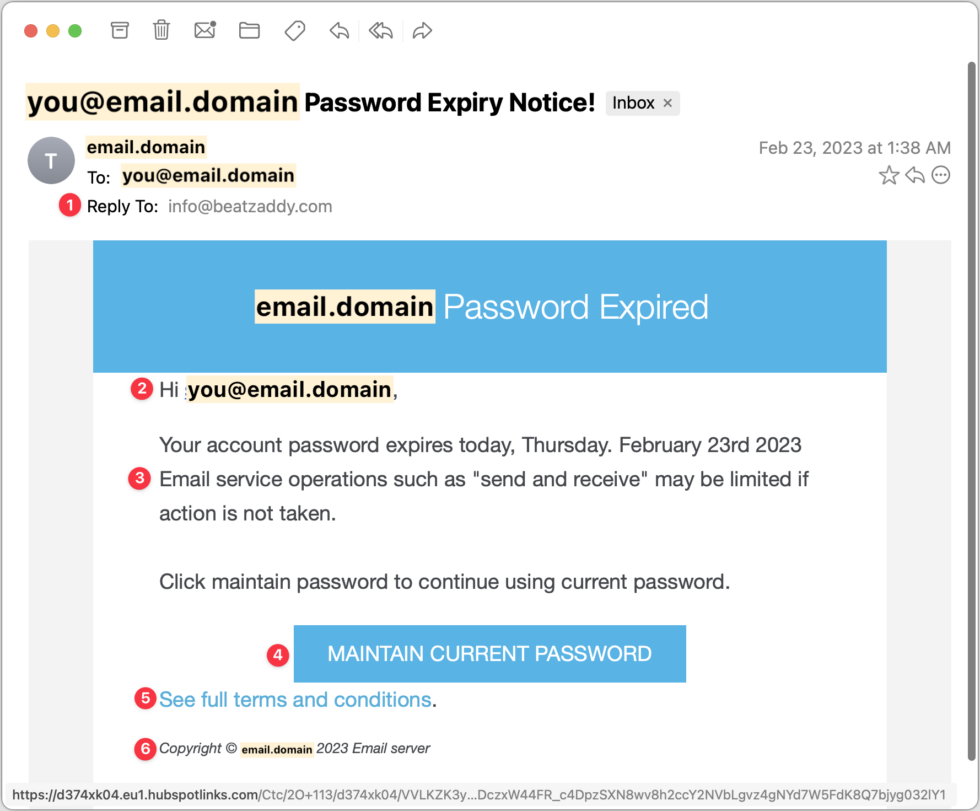
- Note that the Reply-To address is generic and doesn’t match either the email domain used throughout the message or even a major email service provider, which would never send such a message.
- Using your email address instead of your name is something scammers do to make the message seem personalized. If this email really came from your IT support staff, they’d be more likely to use your name or leave the email address out. (Truthfully, they’d never send a message like this.)
- The phrasing and words are not typical of business emails. Using quotes for words like “send and receive” is odd.
- Be careful of things that look like buttons—we’re conditioned to click them without thinking. In many email apps, you can hover the pointer over a button or link to see where it will go. If you look at the URL at the bottom of the window, you can see that it’s completely different from any other domain listed—a clear sign that this is a phishing message.
- “See full terms and conditions” is a strange thing to say in a password-expiration message. What terms and conditions could possibly apply?
- The copyright line is a similar clue. No organization would go to the effort of claiming copyright on a simple support message, and even if it did, it would use its name, not “Email server.”
Spurious Account Access Scam
Our second example pretends to be alerting you to a sign-in to your email account, with the goal of trying to scare you into resetting your password. Frankly, this phishing email stands a good chance of fooling people. You have no way of knowing if your account has been compromised, and if it were compromised, resetting your password is the right thing to do. However, never click through from an email to change a password! You can’t tell if you’re on the right site. Instead, navigate to the site manually, login, and then change the password. While this message is persuasive, it does make some mistakes.
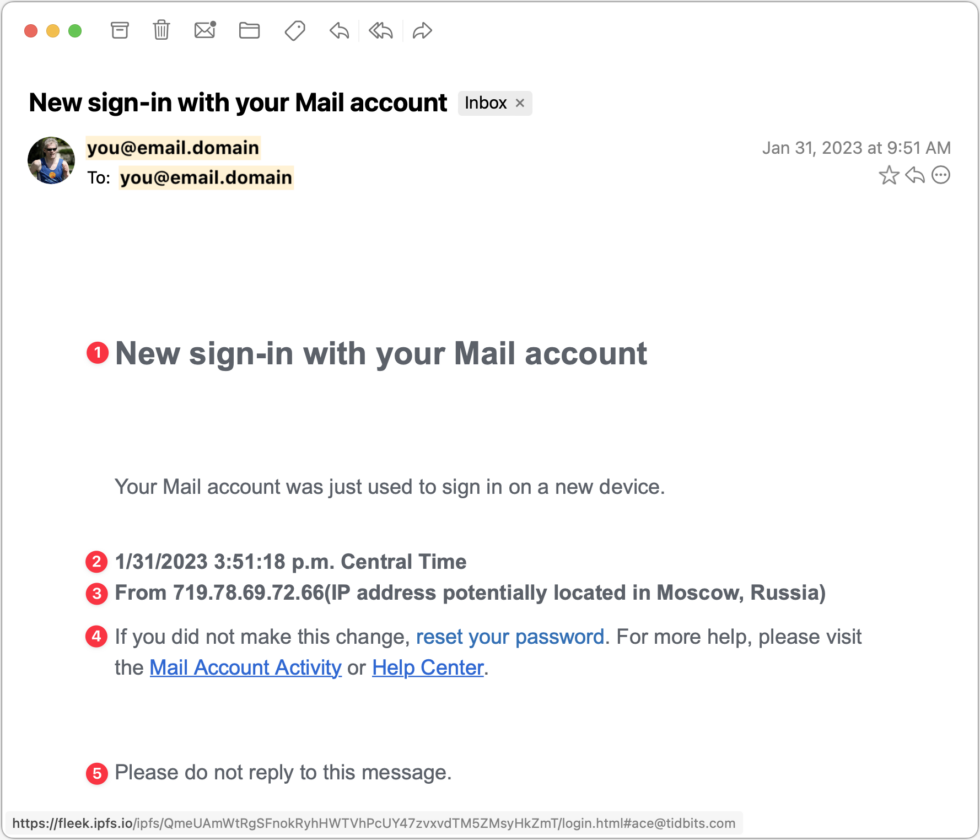
- The capitalization of “Mail” in the Subject and this line should give you pause. Most people wouldn’t capitalize the word, or they’d refer to something more specific, like your “Gmail” or “Outlook” account.
- Another slight strike against this message is the specificity in the timestamp. There’s no reason to include the seconds or the time zone, and most people wouldn’t.
- There are three mistakes in this line that could tip off a savvy Internet user. It claims to provide the IP address from which the sign-in occurred, but real IP addresses are four sets of numbers from 0 to 255. This one has five sets of numbers, the first of which is way too high at 719. The missing space before the parenthetical makes it look wrong, and finally, the parenthetical claim that the IP address is located in Moscow is overdoing it by invoking scary Russian hackers. Of course, this is a pretty technical thing to recognize and most people wouldn’t hone in on this mistake when evaluating if the email is real or fake.
- Note that the “reset your password” link doesn’t have an underline, unlike the other two links. Again, that could happen in a legitimate message, but it’s another slight tell. Hovering over the link reveals the fleek.ipfs.io URL at the bottom—clearly nothing associated with your email account and a dead giveaway.
- A line saying “Please do not reply to this message” is commonplace in transactional messages, so it makes the message seem more real, but a real warning from an IT department would want to make sure you could contact the support staff.
Fraudulent DocuSign Confirmation
Our final example pretends to be confirmation of a document that you’ve already signed in DocuSign. That’s more clever than trying to get you to sign a document (which we’ve seen in other phishing messages) because most people won’t sign something without looking at it carefully. But you might want to see what document this message is talking about and be suckered into clicking through. What’s trickiest about this message is that it has merely changed some of the text in a real DocuSign message, so someone familiar with DocuSign might think it was real. But there are always giveaways.
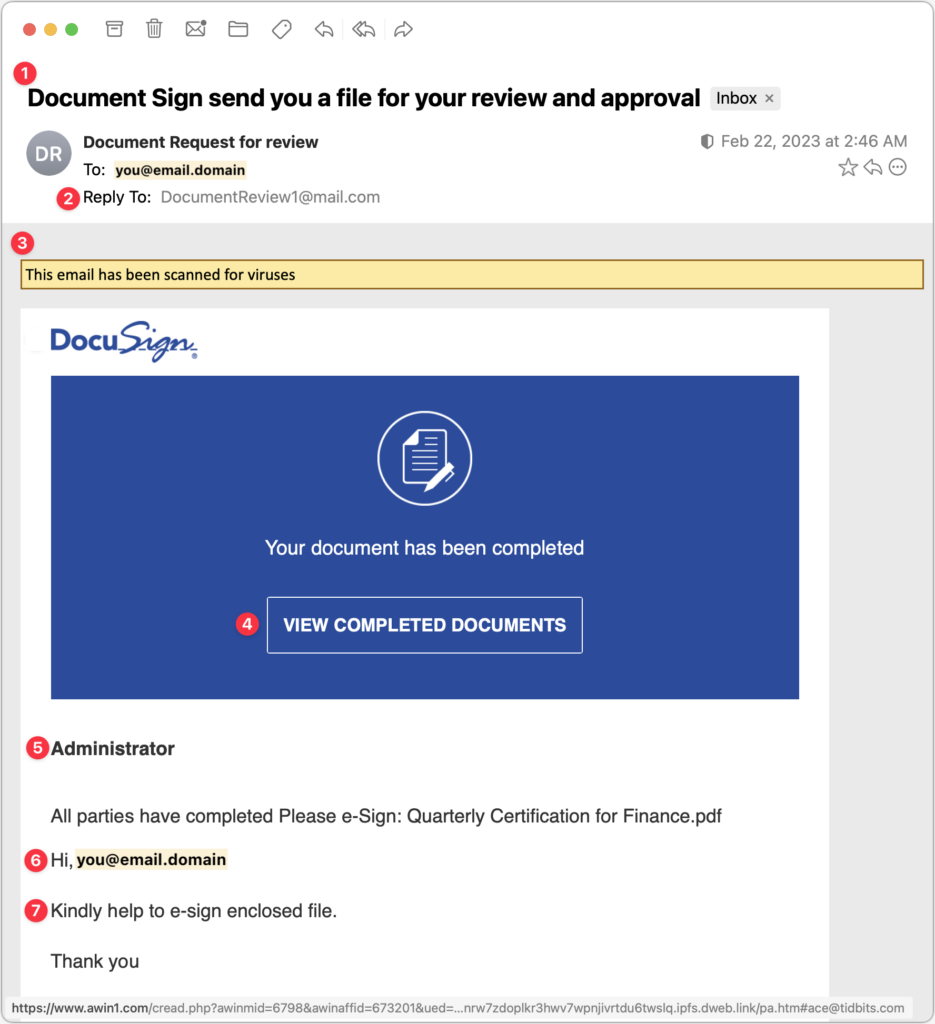
- The subject line of this message is a tell because its grammar is atrocious.
- The Reply-To address should also ring warning bells because it’s so generic that it couldn’t possibly be associated with an actual organization whose documents you are signing.
- The yellow line claiming that the email has been scanned for viruses will likely seem unusual to you—even if an email app presented such a message, it likely wouldn’t do so in the body of the message.
- There’s nothing wrong with the View Completed Documents button, which looks exactly as it would in a real DocuSign message. However, hovering over it reveals the URL at the bottom, which has nothing to do with docusign.net.
- Someone familiar with DocuSign messages might notice that there’s no email address under “Administrator,” as there should be. But that’s not something you would typically notice.
- As with an earlier example, personalizing with an email address is a definite tell. A real person would have entered your name there, if anything.
- This awkward, non-grammatical phrasing is another red flag. Even more problematic is how it asks you to sign the enclosed file, whereas the text and button in the blue box say that the document is completed. The mismatch is a complete giveaway.
We didn’t have room to show the rest of this message, which adds to the verisimilitude by continuing to copy text from a real DocuSign message. The two remaining tells further down are links that are empty when you hover over them and an unknown name in the fine print at the bottom, which reads (bold added for emphasis):
This message was sent to you by sefanya maitimoe who is using the DocuSign Electronic Signature Service. If you would rather not receive email from this sender you may contact the sender with your request.
Overall Advice
Let’s distill what we’ve seen in the examples above into advice you can apply to any message:
- Pay close attention to emails that are very simple, like our second example above, because there’s less they might get wrong.
- With legitimate-looking messages copied from large firms like DocuSign or PayPal, pay special attention to unfamiliar names and email addresses.
- Don’t click anything in an email unless you’ve given it a close-enough look that you’re sure it’s legitimate. It’s too easy to skim and click without thinking, which the scammers count on.
- Read the text of messages with an eye for capitalization, spelling and grammatical mistakes. Scammers could use correct English, but phishing emails often include awkward phrases or non-grammatical language.
- Evaluate any claim about something happening within your organization against what you know to be true. It’s always better to ask someone if passwords need to be reset or accounts are being deactivated instead of assuming a random email message is true.
- Fight the urge to click big, legitimate-looking buttons. Buttons are easy to make and hard to resist, but if you preview the URL under one before clicking, it will often reveal the scam.
- None of our examples fell into this category, but if an email message is just an image that’s being displayed in the body, it’s certainly fake.
Stay safe out there!
About arobasegroup
arobasegroup has been consulting with clients and advising the best use of Apple Technology since 1998. We listen to our customers and solve problems by addressing their specific, unique needs; we never rely on a one-size-fits-all solution or require them to use a specific product. arobasegroup is your advocate in all things related to information technology. Contact us to learn how we can help: info@arobasegroup.com.
Keep Up-to-Date: An Invitation
Keep on top of all the latest Apple-related news via our social media feed. When you follow us on our social media channels, you will always be up-to-date with the most relevant Apple news and have easy access to tips and useful articles relevant for Apple, iPhone, iPad and Apple Watch users. You won’t want to miss these articles and suggestions. Please follow arobasegroup on LinkedIn by tapping here. Thank you!

